Photo by Lukenn Sabellano on Unsplash
OAuth2 and OpenID Connect with WSO2 IS - Part 9
Client Credentials Grant Type
🧬 Introduction
The Client Credentials Grant type provides a secure way for client applications to obtain an Access Token without user authentication. This can be useful in scenarios where the client application needs to access its own resources, such as data storage or APIs, but does not require access to user data. However, it is important to ensure that the client credentials are kept secure, as any party that possesses these credentials can obtain access tokens and access the client's resources.
〰️ Client Credentials Grant Flow
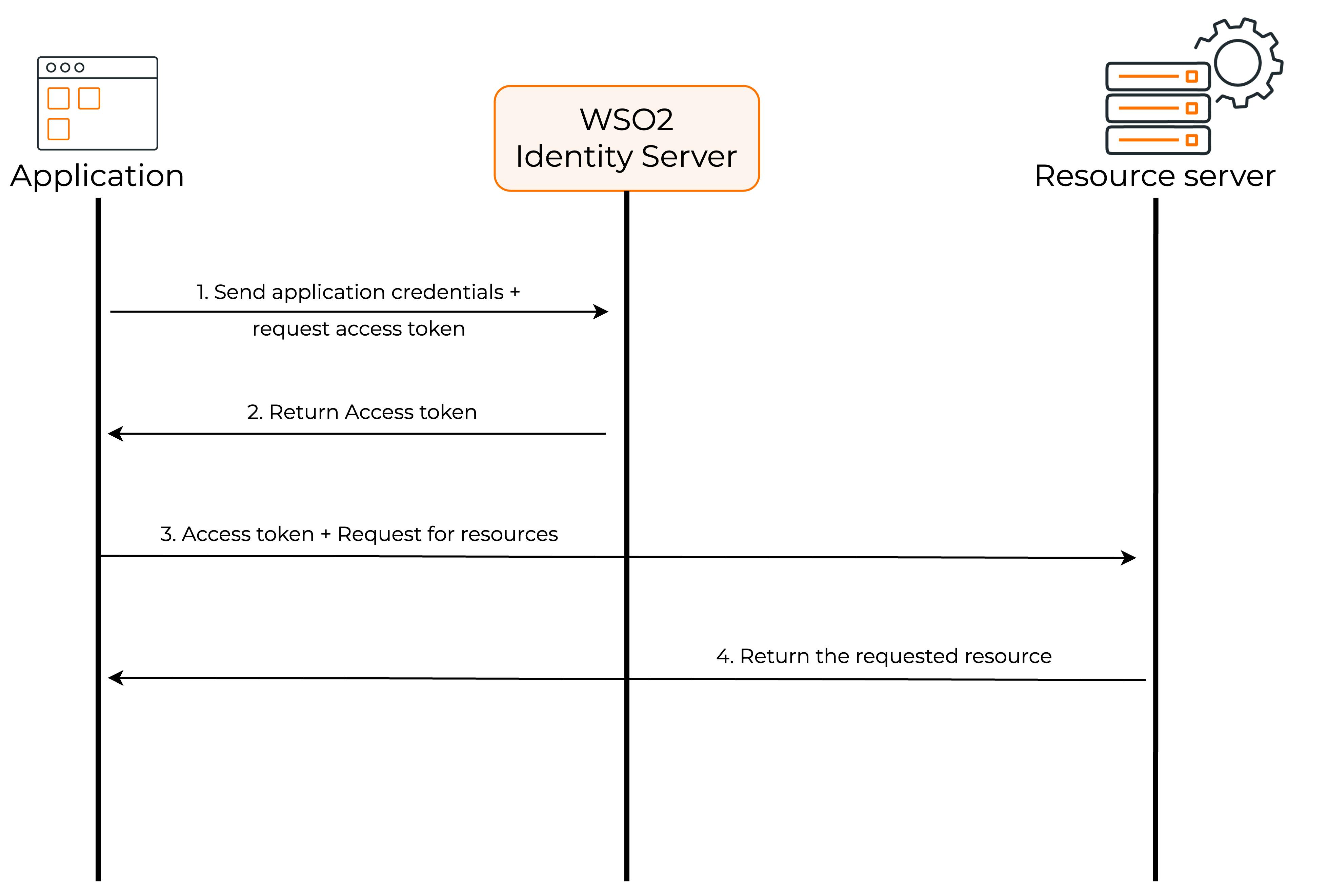
As you can see, the client application sends its credentials( Client ID and Client Secret) to the WSO2 Identity Server and requests an Access Token. The WSO2 Identity Server, which is in this case the Authorization Server sends an Access Token to the client application. The client application can now request user information from the resource server by providing the Access Token.
🧪 Testing Client Credentials Grant Type with WSO2 IS
First, we need to create a Service Provider(SP) in the WSO2 IS. To create a new SP we can use the DCR we have discussed in a previous article.
curl -k -X POST -H "Authorization: Basic YWRtaW46YWRtaW4=" -H "Content-Type: application/json" -d '{"client_name": "playground_2","grant_types": ["authorization_code","password","implicit","client_credentials"], "redirect_uris": ["http://localhost:8080/playground2/oauth2client"],"ext_param_client_id":"provided_client_id0001","ext_param_client_secret":"provided_client_secret0001" }' "https://localhost:9443/api/identity/oauth2/dcr/v1.1/register"
Next, download the Apache Tomcat binary zip file and extract it to a location where you can access it easily on your machine. After that, download the playground2 sample application from WSO2 IS sample releases.
Then put the playground2.war file in the <TOMCAT_HOME>/webapps directory and open a terminal in the <TOMCAT_HOME>/bin directory. Then, run the following commands to extract the playground2.war file.
If permissions are not set
↳
chmod +x catalina.shStart the Tomcat server
↳
./catalina.sh start
After starting the Tomcat server, you will notice there is a directory created in <TOMCAT_HOME>/webapps named playground2. Stop the Tomcat server by typing ./catalina.sh stop and go to <TOMCAT_HOME>/webapps/playground2/WEB-INF/classes and open playground2.properties file. Then provide the Client ID and Client Secret for the playground2 app(When we created the Service Provider(SP) using DCR we gave provided_client_id0001 as the Client ID and provided_client_secret0001 as the Client Secret). After that, start the Tomcat server again by typing ./catalina.sh start in the terminal.

If you want to see the logs of the Tomcat server, open another terminal tab and go to <TOMCAT_HOME>/logs and type, tail -1000f catalina.out
Since our SP is configured properly, we can get the Access Token directly using the below cURL command.
cURL format
↳
curl -u <CLIENT_ID>:<CLIENT_SECRET> -k -d "grant_type=client_credentials&scope=<SCOPES>" -H "Content-Type:application/x-www-form-urlencoded"https://localhost:9443/oauth2/tokencURL example
↳
curl -u provided_client_id0001:provided_client_secret0001 -k -d "grant_type=client_credentials&scope=openid" -H "Content-Type:application/x-www-form-urlencoded"https://localhost:9443/oauth2/token
Note that, we are sending openid as a scope as well. You will notice that even though we send it as a scope or not won't matter when we try to invoke the /oauth2/userinfo endpoint.

It will only give you an Access Token and not an ID Token. This is because you are not using any user credentials to authenticate yourself. You are only using this Client Credentials Grant Type to get an Access Token so that you can access some resources.
Therefore, if you try to use /oauth2/userinfo endpoint to get user-info you will get an error, saying "Access token does not have the openid scope".
So this is it about the Client Credentials Grant Type. We will look at the Refresh Token Grant Type in the next article.