
Photo by Dan Nelson on Unsplash
OAuth2 and OpenID Connect with WSO2 IS - Part 12
SAML2 Bearer Grant Type
Table of contents
🧬 Introduction
SAML2.0 Bearer Grant is a grant type in the OAuth2.0 framework that enables the exchange of a SAML2.0 assertion for an OAuth2.0 token. This grant type is defined in the SAML2.0 Profile for OAuth2.0 Client Authentication and Authorization Grants Specification(RFC 7522).
The SAML2.0 Bearer Grant is a secure method that allows clients to obtain an OAuth2.0 Access Token by presenting a SAML2.0 assertion. This grant type is particularly useful in scenarios where the client already has a SAML assertion from a trusted Identity Provider(IdP) and seeks to exchange it for an Access Token. It offers significant advantages in systems that already utilize SAML for Single Sign-On(SSO), as it enables the client to obtain an Access Token without requiring the user to re-authenticate. To use this grant type, the client submits a request with the SAML assertion to the token endpoint, and following successful authentication and validation, the server issues an access token.
To understand it more, look at the following diagram.

The user sends a login request to the client application.
The client application sends an authentication request to the third-party IdP using SAML2.0.
Upon successful user authentication, the third part IdP issues a SAML2.0 assertion to the client application.
The client application requests token exchange to the authorization server, specifying the SAML2.0 bearer grant type and providing the necessary parameters, such as the original SAML2.0 assertion.
The authorization server validates the SAML2.0 assertion and if valid, generates a new access token of the requested type based on the provided parameters and the server's policy, and responds to the client with the new access token.
The client application can now request resources from the resource server by providing the access token.
As the resource server trusts WSO2 IS-issued tokens, it returns the requested resources to the client application.
🧪 Testing SAML2 Bearer Grant with WSO2 IS
To use SAML2 Bearer Grant we need two WSO2 IS packages. We will use IS-1 and IS-2 to refer them. In addition, we need a SAML2 application to get the SAML assertion. For that, we can use the travelocity.com sample application given by WSO2. You can download it from here. Furthermore, download the playgroud2 application from there as well, since we need to have an OAuth2/OIDC-supported application to test this flow as well. After downloading both applications, download Apache-tomcat from here and put the application .war files of travelocity.com and playground2 inside the <TOMCAT_HOME>/webapps Then go to <TOMCAT_HOME>/bin and type chmod +x catalina.sh to give execute permissions to the catalina.sh file. Finally, run the tomcat server by typing ./catalina.sh start.
Sometimes with the travelocity.com application, there can be signature validation issues and maximum header size exceeded issues. In case, if you have any of those issues first stop the Tomcat server by typing ./catalina.sh stop and follow the below instructions.
Signature validations issues
↳ Go to
<IS_HOME>/repository/resources/securityand copy thewso2carbon.jksandclient-truststore.jksfiles. Then go to<TOMCAT_HOME>/webapps/travelocity.com/WEB-INF/classesand paste and replace the.jksfiles.Maximum header size exceeded issue.
↳ Go to
<TOMCAT_HOME>/confand openserver.xmlfile. Then find the<Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" redirectPort="8443" maxParameterCount="1000" maxHttpHeaderSize="65536"/>and make sure there ismaxHttpHeaderSize="65536"If it does not present in there add it as shown above.
Then, open the IS-1's WSO2 Management Console and create a Service Provider there for the playground2 application. Go to Inbound Authentication Configuration → OAuth/OpenID Connect Configuration. Then make sure to check all the Allowed Grant Types and give http://localhost:8080/playground2/oauth2client as the Callback Url.

Make sure to copy the Client ID and Client Secret for future reference. In my case, they are,
Client ID
↳
provided_client_id0002Client Secret
↳
provided_client_secret0002
I have these human-readable Client ID and Client Secret because I have used the WSO2 IS's DCR endpoint to create the SP. You can check my previous article on DCR to learn about it more.
Next, create another SP for the travelocity.com application. In that case, select Inbound Authentication Configuration → SAML2 Web SSO Configuration. After that make sure to add the following configurations.
Issuer Name → travelocity.com (This should be the same as the webapp name)
Default Assertion Consumer URL →
http://localhost:8080/travelocity.com/home.jspEnable Response Signing → Checked
Enable Signature Validation in Authentication Requests and Logout Requests → Unchecked
Enable Assertion Encryption → Unchecked
Enable Audience Restriction → Checked →
https://localhost:9443/oauth2/tokenEnable Recipient Validation → Checked →
https://localhost:9443/oauth2/token
Next, open the travelocity.com webapp's properties file in <TOMCAT_HOME>/webapps/travelocity.com/WEB-INF/classes/travelocity.properties and apply the following changes.
EnableSAML2SSOLogin →
trueOAuth2.ClientId →
provided_client_id0002OAuth2.ClientSecret →
provided_client_secret0002
The OAuth2.ClientID and OAuth2.ClientSecret parameters should have the Client ID and Client Secret of the playground2 application.

Next, open <IS2_HOME>/repository/conf/deployment.toml file and append the following configuration to the [server] config in there.
[server]
offset = 1
Then create a new SP using the following command.
curl -k -X POST -H "Authorization: Basic YWRtaW46YWRtaW4=" -H "Content-Type: application/json" -d '{"client_name": "wso2application","grant_types": ["authorization_code","password","implicit"], "redirect_uris": ["https://localhost:9443/commonauth"],"ext_param_client_id":"provided_client_id0001","ext_param_client_secret":"provided_client_secret0001" }' "https://localhost:9444/api/identity/oauth2/dcr/v1.1/register"
The above command will create an SP with the following credentials.
Client Name
↳
wso2applicationClient ID
↳
provided_client_id0001Client Secret
↳
provided_client_secret001
Also, enable all the allowed grant types for the wso2application as well.
Next, create a new user in IS-2 by going to Users and Roles→ Add. For my new user I am giving the following credentials.
username
↳
nipunaupassword
↳
nipunau123
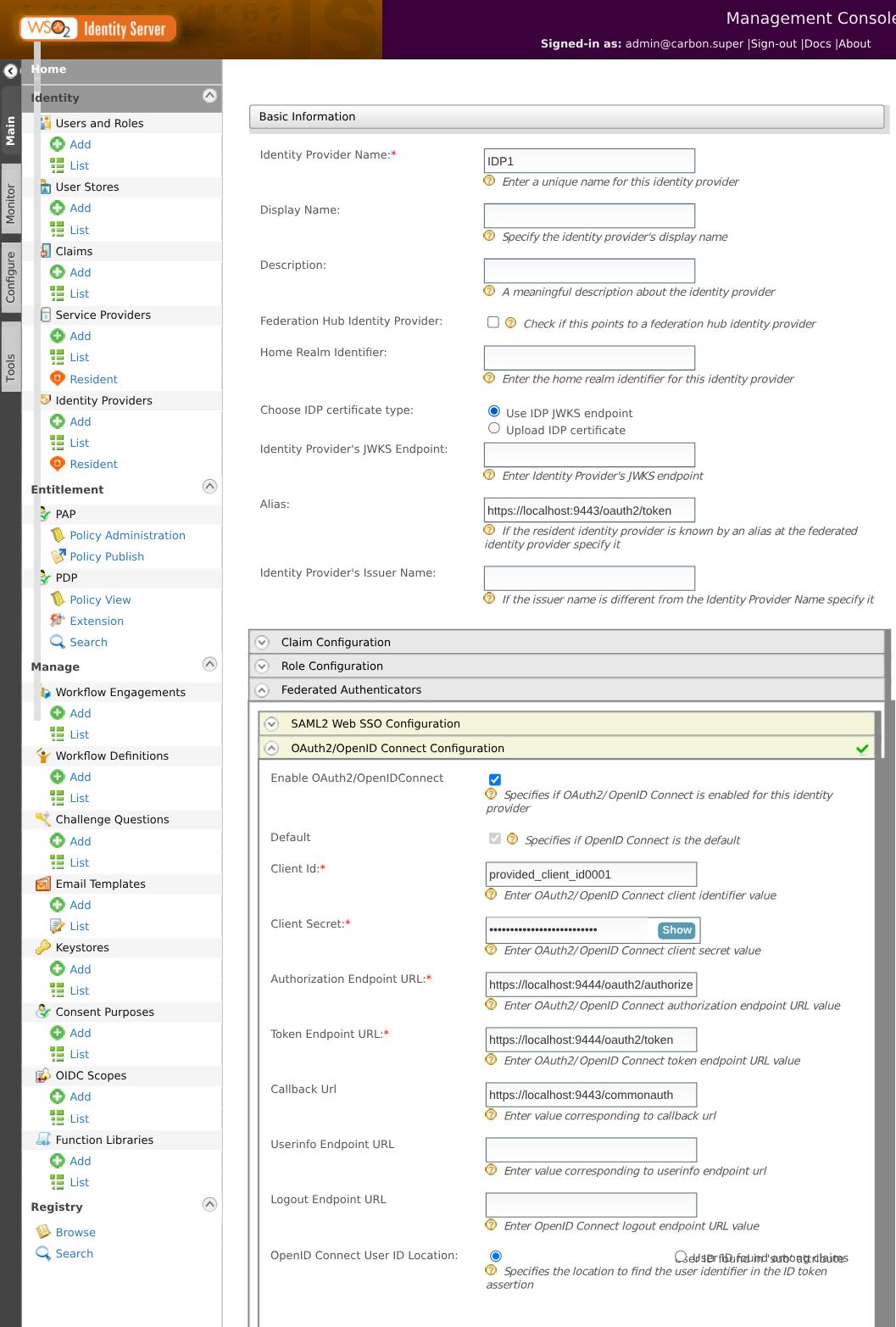
Next, go to the IS-1's Identity Providers → Add. Give it a unique name and go to Federated Authenticators → OAuth2/OpenID Connect Configuration and add the following configurations there.
Enable OAuth2/OpenID Connect
↳ Checked
Client ID
↳
provided_client_id0001Client Secret
↳
provided_client_secret001Authorization Endpoint URL
↳
https://localhost:9444/oauth2/authorizeToken Endpoint URL
↳
https://localhost:9444/oauth2/token
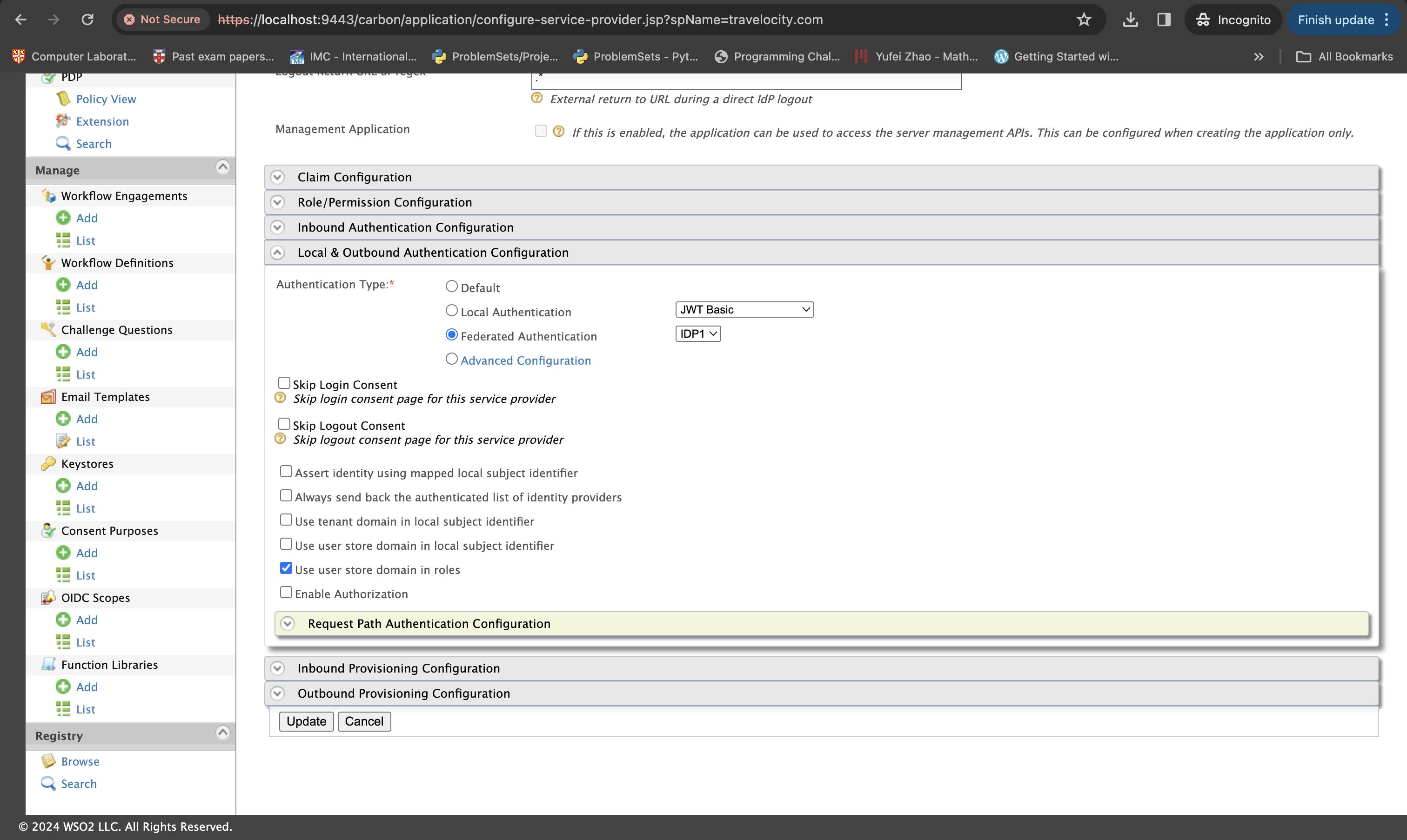
Then go to the Service Providers → List → travelocity.com → Local & Outbound Authentication Configuration and select Federated Authentication and the IdP you have created for the Authentication Type.
Now all the configurations are set to test the SAML2 Bearer Grant type. Open a new browser window in developer mode and type, http://localhost:8080/travelocity.com/index.jsp to view travelocity.com webapp.

Click to login with Redirect Binding and enter the user credentials of the user we created in IS-2.

After you enter the credentials and authenticate you will be redirected to the http://localhost:8080/travelocity.com/home.jsp and you will notice the SAMLResponse parameter in the payload section.

Now you can simply click on the Request OAuth2 Access Token to get an Access Token or use the SAMLResponse to get an Access Token. To do that, first, copy the SAMLResponse and go to https://www.samltool.com/decode.php to decode it.
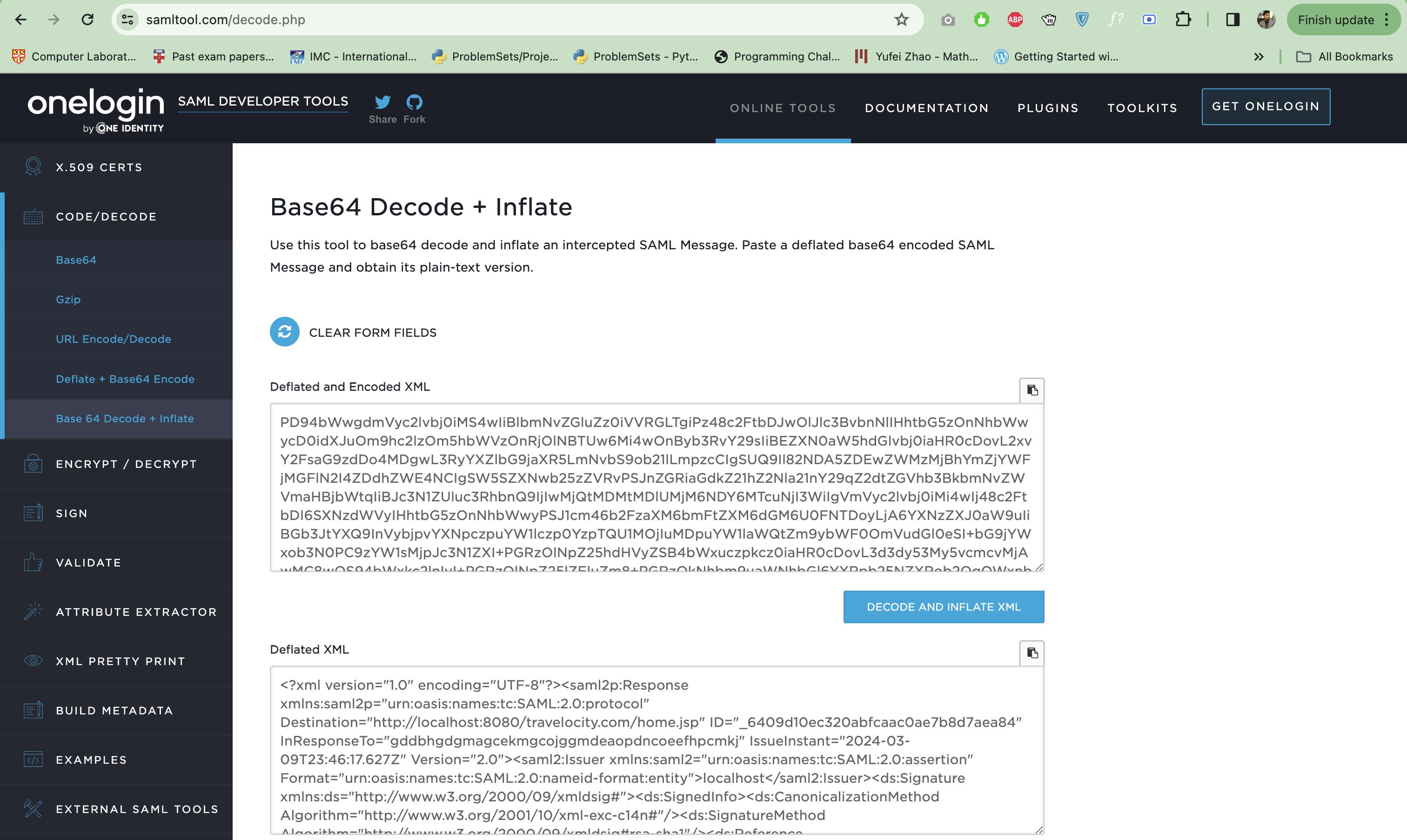
After decoding it copy the section starting with <saml2:Assertion ID="_9fccbbd36d01179f00a67bbe412653be">...</saml2:Assertion> and paste it on https://simplycalc.com/base64url-encode.php to encode it with Base64.

A Sample SAML2 Assertion Data and its Base64 encoded values are shown below.
Data
↳
<saml2:Assertion xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" ID="_9fccbbd36d01179f00a67bbe412653be" IssueInstant="2024-03 09T23:46:17.633Z" Version="2.0"><saml2:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid format:entity">localhost</saml2:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">ds:SignedInfo<ds:Canonical zationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/ <ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa sha1"/><ds:Reference URI="#_9fccbbd36d01179f00a67bbe412653be">ds:Transforms<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/ <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/ </ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>ds:DigestValueuSi70z 4S3oyVnECcI8aVLPztIg=</ds:DigestValue></ds:Reference </ds:SignedInfo>ds:SignatureValueiHzKFgsYCRrmXktFp5IWpMCnsWdIFYyvHL suVj72+ATKR/WEmrfMinOAsQJbAXtocvV6Gt/6hODcja1Ai72hmYaB/KWHcdON 6hzdm+eFjCPLkhu5j/1Z39owWZxtO2sP00i/WGh3rN1+bChwMUDjEDuDkYx7Kb UhjNetnN6I/GpUc7cp7rWF3twe5UceP23e0qdYQ6eHN9kLHEhwLOrUIGq2hyktp m4R2AwNKb0zmv6iZTuNZ/cWREIeX405oVW9f/x4ZGAfiKgK8dC/bP7WSkG1bk CBNTzPEZihCFL9nKwhHav3pr8kw8XRb7ShOilHAuzGqrp8/fkxVKUww= </ds:SignatureValue>ds:KeyInfods:X509Datads:X509CertificateMIIDqTCCApG AwIBAgIEYfEVSjANBgkqhkiG9w0BAQsFADBkMQswCQYDVQQGEwJVUzELMAk A1UECAwCQ0ExFjAUBgNVBAcMDU1vdW50YWluIFZpZXcxDTALBgNVBAoMBF TTzIxDTALBgNVBAsMBFdTTzIxEjAQBgNVBAMMCWxvY2FsaG9zdDAeFw0yMjA MjYwOTMyNThaFw0yNDA0MzAwOTMyNThaMGQxCzAJBgNVBAYTAlVTMQs CQYDVQQIDAJDQTEWMBQGA1UEBwwNTW91bnRhaW4gVmlldzENMAsGA1UE gwEV1NPMjENMAsGA1UECwwEV1NPMjESMBAGA1UEAwwJbG9jYWxob3N0MII IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAkdgncoCrz655Lq8pTdX07 oVBjdZDCUE6ueBd0D1hpJ0/zE3x3Az6tlvzs98PsPuGzaQOMmuLa4qxNJ+OKx mutDUlClpuvxuf+jyq4gCV5tEIILWRMBjlBEpJfWm63+VKKU4nvBWNJ7KfhWjl8 DUdNSh2pCDLpUObmb9Kquqc1x4BgttjN4rx/P+3/v+1jETXzIP1L44yHtpQNv0k Yf4j/aHjcEri9ykvpz1mtdacbrKK25N4V1HHRwDqZiJzOCCISXDuqB6wguY/v4n0l XtrEs7iCyfRFwNSKNrLqr23tR1CscmLfbH6ZLg5CYJTD+1uPSx0HMOB4Wv51P WwIDAQABo2MwYTAUBgNVHREEDTALgglsb2NhbGhvc3QwHQYDVR0OBBYEF 0KQ3YTZJxTsNsPyrZOSFgXXhG+MB0GA1UdJQQWMBQGCCsGAQUFBwMBBgg BgEFBQcDAjALBgNVHQ8EBAMCBPAwDQYJKoZIhvcNAQELBQADggEBAFNJ34C iIlCxmyp27+KA224LaHVtL5DucFK0P22FQ+QKkONiUwO70KoVFreBH1Smxu4e Wk6rMZFOM5oL8HXYg3twy+5eGcL3PQd7X5dwAqlVivzokoi6SDaA/bIG6J/O1U Qd4XEVJdVuLqjk1+cp70ALt0X6B7sNLfjFcbz3jQULNnK8HNvqbn7zQuP10s8p5 2qVkPBA/pjigRDsIWR6p78QESF+TaHFjxfcD6f9cnYie+yEHERtG8k8x5jLFe+odI1 QGZP8Fy0oKT+E/TJ1FBh4rB1FtKylqGeauPu89DnaJ9+kvpNQ94yFmEuhtDByvDi xAqvlin3TPIfy8=</ds:X509Certificate></ds:X509Data></ds:KeyInfo </ds:Signature>saml2:Subject<saml2:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">5e318916 ab07-4c5f-8ed1-a8f00fcb6f6a</saml2:NameID><saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer" <saml2:SubjectConfirmationData InResponseTo="gddbhgdgmagcekmgcojggmdeaopdncoeefhpcmkj" NotOnOrAfter="2024-03-09T23:51:17.627Z" Recipient="http://localhost:8080/travelocity.com/home.jsp"/ </saml2:SubjectConfirmation><saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer" <saml2:SubjectConfirmationData InResponseTo="gddbhgdgmagcekmgcojggmdeaopdncoeefhpcmkj" NotOnOrAfter="2024-03-09T23:51:17.627Z" Recipient="https://localhost:9443/oauth2/token"/ </saml2:SubjectConfirmation></saml2:Subject><saml2:Conditions NotBefore="2024-03-09T23:46:17.633Z" NotOnOrAfter="2024-03 09T23:51:17.627Z">saml2:AudienceRestrictionsaml2:Audiencetravelocity.com< saml2:Audience>saml2:Audiencehttps://localhost:9443/oauth2/token</saml2: udience></saml2:AudienceRestriction></saml2:Conditions <saml2:AuthnStatement AuthnInstant="2024-03-09T23:46:17.551Z" SessionIndex="0814542e-4637-4a9b-aa49 9688ea8d816a">saml2:AuthnContextsaml2:AuthnContextClassRefurn:oasis:an es:tc:SAML:2.0:ac:classes:Password</saml2:AuthnContextClassRef </saml2:AuthnContext></saml2:AuthnStatement></saml2:Assertion>Encoded Result
↳
PHNhbWwyOkFzc2VydGlvbiB4bWxuczpzYW1sMj0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiIgSUQ9Il85ZmNjYmJkMzZkMDExNzlmMDBhNjdiYmU0MTI2NTNiZSIgSXNzdWVJbnN0YW50PSIyMDI0LTAzLTA5VDIzOjQ2OjE3LjYzM1oiIFZlcnNpb249IjIuMCI-PHNhbWwyOklzc3VlciBGb3JtYXQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpuYW1laWQtZm9ybWF0OmVudGl0eSI-bG9jYWxob3N0PC9zYW1sMjpJc3N1ZXI-PGRzOlNpZ25hdHVyZSB4bWxuczpkcz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnIyI-PGRzOlNpZ25lZEluZm8-PGRzOkNhbm9uaWNhbGl6YXRpb25NZXRob2QgQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzEwL3htbC1leGMtYzE0biMiLz48ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI3JzYS1zaGExIi8-PGRzOlJlZmVyZW5jZSBVUkk9IiNfOWZjY2JiZDM2ZDAxMTc5ZjAwYTY3YmJlNDEyNjUzYmUiPjxkczpUcmFuc2Zvcm1zPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjZW52ZWxvcGVkLXNpZ25hdHVyZSIvPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzEwL3htbC1leGMtYzE0biMiLz48L2RzOlRyYW5zZm9ybXM-PGRzOkRpZ2VzdE1ldGhvZCBBbGdvcml0aG09Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyNzaGExIi8-PGRzOkRpZ2VzdFZhbHVlPnVTaTcwenQ0UzNveVZuRUNjSThhVkxQenRJZz08L2RzOkRpZ2VzdFZhbHVlPjwvZHM6UmVmZXJlbmNlPjwvZHM6U2lnbmVkSW5mbz48ZHM6U2lnbmF0dXJlVmFsdWU-aUh6S0Znc1lDUnJtWGt0RnA1SVdwTUNuc1dkSUZZeXZITDdzdVZqNzIrQVRLUi9XRW1yZk1pbk9Bc1FKYkFYdG9jdlY2R3QvNmhPRGNqYTFBaTcyaG1ZYUIvS1dIY2RPTkY2aHpkbStlRmpDUExraHU1ai8xWjM5b3dXWnh0TzJzUDAwaS9XR2gzck4xK2JDaHdNVURqRUR1RGtZeDdLYi9VaGpOZXRuTjZJL0dwVWM3Y3A3cldGM3R3ZTVVY2VQMjNlMHFkWVE2ZUhOOWtMSEVod0xPclVJR3EyaHlrdHBJbTRSMkF3TktiMHptdjZpWlR1TlovY1dSRUllWDQwNW9WVzlmL3g0WkdBZmlLZ0s4ZEMvYlA3V1NrRzFia1VDQk5UelBFWmloQ0ZMOW5Ld2hIYXYzcHI4a3c4WFJiN1NoT2lsSEF1ekdxcnA4L2ZreFZLVXd3PT08L2RzOlNpZ25hdHVyZVZhbHVlPjxkczpLZXlJbmZvPjxkczpYNTA5RGF0YT48ZHM6WDUwOUNlcnRpZmljYXRlPk1JSURxVENDQXBHZ0F3SUJBZ0lFWWZFVlNqQU5CZ2txaGtpRzl3MEJBUXNGQURCa01Rc3dDUVlEVlFRR0V3SlZVekVMTUFrR0ExVUVDQXdDUTBFeEZqQVVCZ05WQkFjTURVMXZkVzUwWVdsdUlGWnBaWGN4RFRBTEJnTlZCQW9NQkZkVFR6SXhEVEFMQmdOVkJBc01CRmRUVHpJeEVqQVFCZ05WQkFNTUNXeHZZMkZzYUc5emREQWVGdzB5TWpBeE1qWXdPVE15TlRoYUZ3MHlOREEwTXpBd09UTXlOVGhhTUdReEN6QUpCZ05WQkFZVEFsVlRNUXN3Q1FZRFZRUUlEQUpEUVRFV01CUUdBMVVFQnd3TlRXOTFiblJoYVc0Z1ZtbGxkekVOTUFzR0ExVUVDZ3dFVjFOUE1qRU5NQXNHQTFVRUN3d0VWMU5QTWpFU01CQUdBMVVFQXd3SmJHOWpZV3hvYjNOME1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBa2RnbmNvQ3J6NjU1THE4cFRkWDA3ZW9WQmpkWkRDVUU2dWVCZDBEMWhwSjAvekUzeDNBejZ0bHZ6czk4UHNQdUd6YVFPTW11TGE0cXhOSitPS3hKbXV0RFVsQ2xwdXZ4dWYranlxNGdDVjV0RUlJTFdSTUJqbEJFcEpmV202MytWS0tVNG52QldOSjdLZmhXamw4K0RVZE5TaDJwQ0RMcFVPYm1iOUtxdXFjMXg0Qmd0dGpONHJ4L1ArMy92KzFqRVRYeklQMUw0NHlIdHBRTnYwa2hZZjRqL2FIamNFcmk5eWt2cHoxbXRkYWNicktLMjVONFYxSEhSd0RxWmlKek9DQ0lTWER1cUI2d2d1WS92NG4wbDFYdHJFczdpQ3lmUkZ3TlNLTnJMcXIyM3RSMUNzY21MZmJINlpMZzVDWUpURCsxdVBTeDBITU9CNFd2NTFQYld3SURBUUFCbzJNd1lUQVVCZ05WSFJFRURUQUxnZ2xzYjJOaGJHaHZjM1F3SFFZRFZSME9CQllFRkgwS1EzWVRaSnhUc05zUHlyWk9TRmdYWGhHK01CMEdBMVVkSlFRV01CUUdDQ3NHQVFVRkJ3TUJCZ2dyQmdFRkJRY0RBakFMQmdOVkhROEVCQU1DQlBBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFGTkozNENJaUlsQ3hteXAyNytLQTIyNExhSFZ0TDVEdWNGSzBQMjJGUStRS2tPTmlVd083MEtvVkZyZUJIMVNteHU0ZVBXazZyTVpGT001b0w4SFhZZzN0d3krNWVHY0wzUFFkN1g1ZHdBcWxWaXZ6b2tvaTZTRGFBL2JJRzZKL08xVTlRZDRYRVZKZFZ1THFqazErY3A3MEFMdDBYNkI3c05MZmpGY2J6M2pRVUxObks4SE52cWJuN3pRdVAxMHM4cDV5MnFWa1BCQS9wamlnUkRzSVdSNnA3OFFFU0YrVGFIRmp4ZmNENmY5Y25ZaWUreUVIRVJ0RzhrOHg1akxGZStvZEkxL1FHWlA4Rnkwb0tUK0UvVEoxRkJoNHJCMUZ0S3lscUdlYXVQdTg5RG5hSjkra3ZwTlE5NHlGbUV1aHREQnl2RGlqeEFxdmxpbjNUUElmeTg9PC9kczpYNTA5Q2VydGlmaWNhdGU-PC9kczpYNTA5RGF0YT48L2RzOktleUluZm8-PC9kczpTaWduYXR1cmU-PHNhbWwyOlN1YmplY3Q-PHNhbWwyOk5hbWVJRCBGb3JtYXQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjEuMTpuYW1laWQtZm9ybWF0OmVtYWlsQWRkcmVzcyI-NWUzMTg5MTYtYWIwNy00YzVmLThlZDEtYThmMDBmY2I2ZjZhPC9zYW1sMjpOYW1lSUQ-PHNhbWwyOlN1YmplY3RDb25maXJtYXRpb24gTWV0aG9kPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6Y206YmVhcmVyIj48c2FtbDI6U3ViamVjdENvbmZpcm1hdGlvbkRhdGEgSW5SZXNwb25zZVRvPSJnZGRiaGdkZ21hZ2Nla21nY29qZ2dtZGVhb3BkbmNvZWVmaHBjbWtqIiBOb3RPbk9yQWZ0ZXI9IjIwMjQtMDMtMDlUMjM6NTE6MTcuNjI3WiIgUmVjaXBpZW50PSJodHRwOi8vbG9jYWxob3N0OjgwODAvdHJhdmVsb2NpdHkuY29tL2hvbWUuanNwIi8-PC9zYW1sMjpTdWJqZWN0Q29uZmlybWF0aW9uPjxzYW1sMjpTdWJqZWN0Q29uZmlybWF0aW9uIE1ldGhvZD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmNtOmJlYXJlciI-PHNhbWwyOlN1YmplY3RDb25maXJtYXRpb25EYXRhIEluUmVzcG9uc2VUbz0iZ2RkYmhnZGdtYWdjZWttZ2NvamdnbWRlYW9wZG5jb2VlZmhwY21raiIgTm90T25PckFmdGVyPSIyMDI0LTAzLTA5VDIzOjUxOjE3LjYyN1oiIFJlY2lwaWVudD0iaHR0cHM6Ly9sb2NhbGhvc3Q6OTQ0My9vYXV0aDIvdG9rZW4iLz48L3NhbWwyOlN1YmplY3RDb25maXJtYXRpb24-PC9zYW1sMjpTdWJqZWN0PjxzYW1sMjpDb25kaXRpb25zIE5vdEJlZm9yZT0iMjAyNC0wMy0wOVQyMzo0NjoxNy42MzNaIiBOb3RPbk9yQWZ0ZXI9IjIwMjQtMDMtMDlUMjM6NTE6MTcuNjI3WiI-PHNhbWwyOkF1ZGllbmNlUmVzdHJpY3Rpb24-PHNhbWwyOkF1ZGllbmNlPnRyYXZlbG9jaXR5LmNvbTwvc2FtbDI6QXVkaWVuY2U-PHNhbWwyOkF1ZGllbmNlPmh0dHBzOi8vbG9jYWxob3N0Ojk0NDMvb2F1dGgyL3Rva2VuPC9zYW1sMjpBdWRpZW5jZT48L3NhbWwyOkF1ZGllbmNlUmVzdHJpY3Rpb24-PC9zYW1sMjpDb25kaXRpb25zPjxzYW1sMjpBdXRoblN0YXRlbWVudCBBdXRobkluc3RhbnQ9IjIwMjQtMDMtMDlUMjM6NDY6MTcuNTUxWiIgU2Vzc2lvbkluZGV4PSIwODE0NTQyZS00NjM3LTRhOWItYWE0OS05Njg4ZWE4ZDgxNmEiPjxzYW1sMjpBdXRobkNvbnRleHQ-PHNhbWwyOkF1dGhuQ29udGV4dENsYXNzUmVmPnVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphYzpjbGFzc2VzOlBhc3N3b3JkPC9zYW1sMjpBdXRobkNvbnRleHRDbGFzc1JlZj48L3NhbWwyOkF1dGhuQ29udGV4dD48L3NhbWwyOkF1dGhuU3RhdGVtZW50Pjwvc2FtbDI6QXNzZXJ0aW9uPg==
Next, run the following cURL command to get the Access Token for the playground2 application.
cURL format
↳
curl -k --location 'https://localhost:9443/oauth2/token' --header 'Content-Type: application/x-www-form-urlencoded' --header 'Authorization: Basic <base64(CLIENT_ID:CLIENT_SECRET)>' --data-urlencode 'grant_type=urn:ietf:params:oauth:grant-type:saml2-bearer' --data-urlencode 'assertion=<base64(SAML_ASSERTION)>' --data-urlencode 'scope=openid'Sample cURL
↳
curl -k --location 'https://localhost:9443/oauth2/token' --header 'Content-Type: application/x-www-form-urlencoded' --header 'Authorization: Basic cHJvdmlkZWRfY2xpZW50X2lkMDAwMjpwcm92aWRlZF9jbGllbnRfc2VjcmV0MDAwMg==' --data-urlencode 'grant_type=urn:ietf:params:oauth:grant-type:saml2-bearer' --data-urlencode 'assertion=PHNhbWwyOkFzc2VydGlvbiB4bWxuczpzYW1sMj0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiIgSUQ9Il8xZGU2MzM2MWRlNTIwMmM3NDczMGQwOGM2NDU3NDQ5OCIgSXNzdWVJbnN0YW50PSIyMDI0LTAzLTEwVDAwOjAwOjI2LjEyOFoiIFZlcnNpb249IjIuMCI-PHNhbWwyOklzc3VlciBGb3JtYXQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpuYW1laWQtZm9ybWF0OmVudGl0eSI-bG9jYWxob3N0PC9zYW1sMjpJc3N1ZXI-PGRzOlNpZ25hdHVyZSB4bWxuczpkcz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnIyI-PGRzOlNpZ25lZEluZm8-PGRzOkNhbm9uaWNhbGl6YXRpb25NZXRob2QgQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzEwL3htbC1leGMtYzE0biMiLz48ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI3JzYS1zaGExIi8-PGRzOlJlZmVyZW5jZSBVUkk9IiNfMWRlNjMzNjFkZTUyMDJjNzQ3MzBkMDhjNjQ1NzQ0OTgiPjxkczpUcmFuc2Zvcm1zPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjZW52ZWxvcGVkLXNpZ25hdHVyZSIvPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzEwL3htbC1leGMtYzE0biMiLz48L2RzOlRyYW5zZm9ybXM-PGRzOkRpZ2VzdE1ldGhvZCBBbGdvcml0aG09Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyNzaGExIi8-PGRzOkRpZ2VzdFZhbHVlPkZCaFZIdUowVkpLN3hOTU5ibEhBdzM3WFJOMD08L2RzOkRpZ2VzdFZhbHVlPjwvZHM6UmVmZXJlbmNlPjwvZHM6U2lnbmVkSW5mbz48ZHM6U2lnbmF0dXJlVmFsdWU-Tk5jMmtXMGhWcVlYc0xLV2hONHRqZ1l6VWhyUVVucmZuTzdWN093OXdBVWhjd1g2Mld6QVlBNjZvZHVYZXA5ZFZianowNzlOUVhnUXNCWStwd2l5YUJ2S3djZ0dZT2wxeGxjb1A2amhsK3hmU0dLTkowYTFoRXFCaklORDNvTEI0bnlLU1Z0UlR4VW02a21XOGE3aXZadGJWb2kxK1VLSGk2Z21JdEcxdFd6U2hPdUxFMGQxTHZENVlpTmdLZmx1QUFMT3FzWjZIbEtobHd1aVFOUzJSZ0xLYmNEekVwUndRckJJMjM0NlBlZVpXbnkxRzRVb2JIakVGbjYvUnhiN1hiSENOSzZqR0VUbXA2MWY3NXhsZGE0T29zZGhlaVNoTEFFU2lTQjlWSjYzckx5QW5SVmN2RW81Qk5jQ2szWk9JYzVhYUJmSkRwaFpmS1VaUHpiNzRBPT08L2RzOlNpZ25hdHVyZVZhbHVlPjxkczpLZXlJbmZvPjxkczpYNTA5RGF0YT48ZHM6WDUwOUNlcnRpZmljYXRlPk1JSURxVENDQXBHZ0F3SUJBZ0lFWWZFVlNqQU5CZ2txaGtpRzl3MEJBUXNGQURCa01Rc3dDUVlEVlFRR0V3SlZVekVMTUFrR0ExVUVDQXdDUTBFeEZqQVVCZ05WQkFjTURVMXZkVzUwWVdsdUlGWnBaWGN4RFRBTEJnTlZCQW9NQkZkVFR6SXhEVEFMQmdOVkJBc01CRmRUVHpJeEVqQVFCZ05WQkFNTUNXeHZZMkZzYUc5emREQWVGdzB5TWpBeE1qWXdPVE15TlRoYUZ3MHlOREEwTXpBd09UTXlOVGhhTUdReEN6QUpCZ05WQkFZVEFsVlRNUXN3Q1FZRFZRUUlEQUpEUVRFV01CUUdBMVVFQnd3TlRXOTFiblJoYVc0Z1ZtbGxkekVOTUFzR0ExVUVDZ3dFVjFOUE1qRU5NQXNHQTFVRUN3d0VWMU5QTWpFU01CQUdBMVVFQXd3SmJHOWpZV3hvYjNOME1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBa2RnbmNvQ3J6NjU1THE4cFRkWDA3ZW9WQmpkWkRDVUU2dWVCZDBEMWhwSjAvekUzeDNBejZ0bHZ6czk4UHNQdUd6YVFPTW11TGE0cXhOSitPS3hKbXV0RFVsQ2xwdXZ4dWYranlxNGdDVjV0RUlJTFdSTUJqbEJFcEpmV202MytWS0tVNG52QldOSjdLZmhXamw4K0RVZE5TaDJwQ0RMcFVPYm1iOUtxdXFjMXg0Qmd0dGpONHJ4L1ArMy92KzFqRVRYeklQMUw0NHlIdHBRTnYwa2hZZjRqL2FIamNFcmk5eWt2cHoxbXRkYWNicktLMjVONFYxSEhSd0RxWmlKek9DQ0lTWER1cUI2d2d1WS92NG4wbDFYdHJFczdpQ3lmUkZ3TlNLTnJMcXIyM3RSMUNzY21MZmJINlpMZzVDWUpURCsxdVBTeDBITU9CNFd2NTFQYld3SURBUUFCbzJNd1lUQVVCZ05WSFJFRURUQUxnZ2xzYjJOaGJHaHZjM1F3SFFZRFZSME9CQllFRkgwS1EzWVRaSnhUc05zUHlyWk9TRmdYWGhHK01CMEdBMVVkSlFRV01CUUdDQ3NHQVFVRkJ3TUJCZ2dyQmdFRkJRY0RBakFMQmdOVkhROEVCQU1DQlBBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFGTkozNENJaUlsQ3hteXAyNytLQTIyNExhSFZ0TDVEdWNGSzBQMjJGUStRS2tPTmlVd083MEtvVkZyZUJIMVNteHU0ZVBXazZyTVpGT001b0w4SFhZZzN0d3krNWVHY0wzUFFkN1g1ZHdBcWxWaXZ6b2tvaTZTRGFBL2JJRzZKL08xVTlRZDRYRVZKZFZ1THFqazErY3A3MEFMdDBYNkI3c05MZmpGY2J6M2pRVUxObks4SE52cWJuN3pRdVAxMHM4cDV5MnFWa1BCQS9wamlnUkRzSVdSNnA3OFFFU0YrVGFIRmp4ZmNENmY5Y25ZaWUreUVIRVJ0RzhrOHg1akxGZStvZEkxL1FHWlA4Rnkwb0tUK0UvVEoxRkJoNHJCMUZ0S3lscUdlYXVQdTg5RG5hSjkra3ZwTlE5NHlGbUV1aHREQnl2RGlqeEFxdmxpbjNUUElmeTg9PC9kczpYNTA5Q2VydGlmaWNhdGU-PC9kczpYNTA5RGF0YT48L2RzOktleUluZm8-PC9kczpTaWduYXR1cmU-PHNhbWwyOlN1YmplY3Q-PHNhbWwyOk5hbWVJRCBGb3JtYXQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjEuMTpuYW1laWQtZm9ybWF0OmVtYWlsQWRkcmVzcyI-NWUzMTg5MTYtYWIwNy00YzVmLThlZDEtYThmMDBmY2I2ZjZhPC9zYW1sMjpOYW1lSUQ-PHNhbWwyOlN1YmplY3RDb25maXJtYXRpb24gTWV0aG9kPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6Y206YmVhcmVyIj48c2FtbDI6U3ViamVjdENvbmZpcm1hdGlvbkRhdGEgSW5SZXNwb25zZVRvPSJjcHBlYWRpa2NiYm5rZmVjbGlsaW5obmNrbmFiYmNjb29wY2pmamVjIiBOb3RPbk9yQWZ0ZXI9IjIwMjQtMDMtMTBUMDA6MDU6MjYuMTI3WiIgUmVjaXBpZW50PSJodHRwOi8vbG9jYWxob3N0OjgwODAvdHJhdmVsb2NpdHkuY29tL2hvbWUuanNwIi8-PC9zYW1sMjpTdWJqZWN0Q29uZmlybWF0aW9uPjxzYW1sMjpTdWJqZWN0Q29uZmlybWF0aW9uIE1ldGhvZD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmNtOmJlYXJlciI-PHNhbWwyOlN1YmplY3RDb25maXJtYXRpb25EYXRhIEluUmVzcG9uc2VUbz0iY3BwZWFkaWtjYmJua2ZlY2xpbGluaG5ja25hYmJjY29vcGNqZmplYyIgTm90T25PckFmdGVyPSIyMDI0LTAzLTEwVDAwOjA1OjI2LjEyN1oiIFJlY2lwaWVudD0iaHR0cHM6Ly9sb2NhbGhvc3Q6OTQ0My9vYXV0aDIvdG9rZW4iLz48L3NhbWwyOlN1YmplY3RDb25maXJtYXRpb24-PC9zYW1sMjpTdWJqZWN0PjxzYW1sMjpDb25kaXRpb25zIE5vdEJlZm9yZT0iMjAyNC0wMy0xMFQwMDowMDoyNi4xMjhaIiBOb3RPbk9yQWZ0ZXI9IjIwMjQtMDMtMTBUMDA6MDU6MjYuMTI3WiI-PHNhbWwyOkF1ZGllbmNlUmVzdHJpY3Rpb24-PHNhbWwyOkF1ZGllbmNlPnRyYXZlbG9jaXR5LmNvbTwvc2FtbDI6QXVkaWVuY2U-PHNhbWwyOkF1ZGllbmNlPmh0dHBzOi8vbG9jYWxob3N0Ojk0NDMvb2F1dGgyL3Rva2VuPC9zYW1sMjpBdWRpZW5jZT48L3NhbWwyOkF1ZGllbmNlUmVzdHJpY3Rpb24-PC9zYW1sMjpDb25kaXRpb25zPjxzYW1sMjpBdXRoblN0YXRlbWVudCBBdXRobkluc3RhbnQ9IjIwMjQtMDMtMTBUMDA6MDA6MjYuMTIxWiIgU2Vzc2lvbkluZGV4PSIzYzYyNGU0My03MjBlLTRmZDctYTE5Ny1hNjY1ODk1YTBkMzkiPjxzYW1sMjpBdXRobkNvbnRleHQ-PHNhbWwyOkF1dGhuQ29udGV4dENsYXNzUmVmPnVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphYzpjbGFzc2VzOlBhc3N3b3JkPC9zYW1sMjpBdXRobkNvbnRleHRDbGFzc1JlZj48L3NhbWwyOkF1dGhuQ29udGV4dD48L3NhbWwyOkF1dGhuU3RhdGVtZW50Pjwvc2FtbDI6QXNzZXJ0aW9uPg==' --data-urlencode 'scope=openid'
After executing the above cURL request, you will get an Access Token and an ID Token.

After getting the Access Token you can check the /oauth2/userinfo endpoint using that.
cURL format
↳
curl -k -v -H "Authorization: Bearer <ACCESS_TOKEN>" https://localhost:9443/oauth2/userinfoSample cURL
↳
curl -k -v -H "Authorization: Bearer 17b04dfa-939d-3d26-a7bd-b15c7111d8b3 " https://localhost:9443/oauth2/userinfo
Rather than using an additional external IdP(IS-2), we can do this with a single IS as well. To do that, first, add the following configuration to the <IS1_HOME>/repository/conf/deployment.toml
[oauth.grant_type.saml_bearer]
user_type= "LOCAL"
Then go to the Service Providers → List → travelocity.com → Local & Outbound Authentication Configuration and select the default for the Authentication Type. Afterward, you can log in to the travelocity.com app again by going to the http://localhost:8080/travlocity.com/index.jsp and repeat the steps we have discussed above.
So this is it about the SAML2 Bearer Grant Type. In the next article, we will look at how Session Management is done with OIDC in WSO2 IS.
